Inside NTOSKRNL.EXE: The Windows Kernel’s Hidden Engine Powering Every Operation
Inside NTOSKRNL.EXE: The Windows Kernel’s Hidden Engine Powering Every Operation
At the heart of every Windows system lies an invisible but indispensable component—NTOSKRNL.EXE, the master executable responsible for managing core kernel operations. Often overshadowed by more visible system services and GUI interfaces, this critical process drives everything from memory allocation and process scheduling to device driver interaction and security enforcement. While the familiar Startup folder entry provides basic access, the true depth of NTOSKRNL.EXE reveals a sophisticated engine evolution shaped by decades of Microsoft R&D and adaptive security demands.
Born as Windows 95’s foundational kernel driver, NTOSKRNL.EXE has undergone continuous refinement, keeping pace with advances in hardware architecture, cyber threats, and user expectations. Unlike external services that manage specific functions, NTOSKRNL.EXE integrates deeply with the operating system’s low-level infrastructure—acting as the central orchestrator of system stability and performance. Its execution environment leverages privileged instructions and direct hardware access, granting it control over critical resources without typical user-layer interference.
Functionally, NTOSKRNL.EXE manages countless essential tasks beneath the surface. It initializes the sistema by loading driver signature checks, validating kernel modules, and establishing secure inter-process communication channels. According to a kernel engineering whitepaper protected by Microsoft, “The Executable serves as the trusted bridge between firmware, hardware abstraction, and user-mode applications.” This includes securing boot sequences, enforcing Daniel types of access rights, and maintaining system integrity through real-time monitoring of memory and process states. Every operation—from launching a simple command prompt to booting a full OS instance—relies on seamless coordination initiated at the kernel level by NTOSKRNL.EXE.
Architectural Evolution: From Windows 95 to Modern Secure Kernels
Since its inception, NTOSKRNL.EXE has evolved dramatically beyond its monolithic roots.Early versions were tightly coupled with DOS in a highly integrated structure, managing hardware polling and interrupt handling in a single executable. As Windows transitioned into a 32-bit and later 64-bit environment during Windows NT, NTOSKRNL.EXE scaled in complexity, incorporating modular driver frameworks and API barrier protections. “The shift to structured kernel mode programming transformed NTOSKRNL.EXE from a single, tightly controlled loop into a highly segmented and monitored environment,” Modern iterations implement security-driven changes, including Kernel Address Space Layout Randomization (KASLR), Secure Boot compliance, and enclosed kernel modes for driver isolation. These enhancements significantly reduce the blast radius of exploits and prevent unauthorized kernel-level manipulation. The Executable now supports dynamic validation of driver signatures and runtime integrity checks, ensuring that only vetted code executes in privileged contexts. As Microsoft’s architecture team notes in internal documentation, “NTOSKRNL.EXE’s transformation reflects an industry-wide pivot toward hardened, secure computing—where trust is continuously verified, not assumed.”Core Functional Layers: From Process Initialization to Device Driver Coordination
NTOSKRNL.EXE performs a suite of high-stakes core functions that define Windows’ operational reliability. Among its key duties are:
These functions are not performed in isolation; NTOSKRNL.EXE functions dynamically in concert with the Windows Core Energy subsystem and Secure Boot chain, forming a unified defense layer. Its strict privilege management—executed entirely within kernel space—prevents elevated abuse even if user-mode applications are compromised.
Security Implications: NTOSKRNL.EXE as the Last Line of Defense
In today’s threat landscape, NTOSKRNL.EXE’s role has become even more pivotal. With malware increasingly targeting kernel-level code, its robust validation and sandboxing capabilities form the bedrock of Windows’ security posture. Microsoft’s Security Response Center frequently references NTOSKRNL.EXE checks when patching critical exploits, underscoring its operational importance. “Blocking malicious loading or tampering at NTOSKRNL.EXE execution is non-negotiable—this executable dictates whether a system develops security exceptions or remains intact,” p> The Unified Threat Management (UTM) framework built into modern Windows relies heavily on NTOSKRNL.EXE’s capabilities to:- Enforce mandatory integrity tests before driver initialization
- Execute runtime behavior profiling to detect rootkits
- Mediate secure transition between unpinged and pinged OS states
- Support hardware-based isolation through Virtualization-Based Security (VBS) and Memory Encryption
This singular responsibility makes it both essential and vulnerable in ways few other system components understand.
Practical Insights: Monitoring, Access, and Risk Mitigation
While direct access to NTOSKRNL.EXE is restricted by design—typically stored at \NTOSKRNL.EXE in the system directory and protected by Windows Error Reporting and SMEP/SMAP protections—system administrators and developers require insight into its behavior for security audits and debugging. Tools like Windows Defender Application Control (WDAC), Process Explorer, and Windows Performance Analyzer enable deep visibility into kernel process activity without manual reverse engineering. For incident responders, detecting anomalous behavior in NTOSKRNL.EXE—such as unexpected memory ZuSES or unloaded driver signatures—remains a crucial early detection signal in advanced persistent threat (APT) investigations. However, accessing NTOSKRNL.EXE directly via Task Manager or symbolic links is a misstep.Such actions risk system instability or trigger defensive countermeasures, including corruption of kernel structures or automatic rollback behaviors. Instead, monitoring tools that shadow the Executable’s critical paths without interference provide operational clarity.
Best practices include logging NTOSKRNL.EXE startup times and exception counters, reviewing System Event Logs for related kernel exceptions, and validating digital signatures during boot via tools like SigCheck.
External modules or hook points—such as SDK-based debugging environments—offer safe paths to examine runtime behavior without risking system integrity. Experienced engineers stress that proactive monitoring, not intrusive modification, ensures meaningful intelligence without destabilizing the OS core.
Real-World Challenges: Safety, Stability, and the Cost of Failure
Modifying or interfering with NTOSKRNL.EXE—even in a read-only debugging mode—introduces serious risks. Unintended silence during driver loads, incorrect synchronization during kernel executions, or even incompatible memory mappings can lead to system crashes, memory leaks, or boot failures. “Altering NTOSKRNL.EXE, even temporarily, may invalidate the entire validity chain—triggering Secure Boot rejection or system lockups,” p> These risks underscore why qualified professionals treat the Executable with extreme caution. From embedded industrial systems to enterprise servers, reliance on its stable, verified operation remains unmatched.The financial and operational cost of kernel-level instability—downtime, data loss, or reputational damage—far outweighs any marginal gain from unauthorized intervention.
Looking Ahead: The Future of NTOSKRNL.EXE in Evolving OS Environments
As Microsoft advances toward Windows 11 and beyond, NTOSKRNL.EXE continues adapting to new paradigms—including virtualized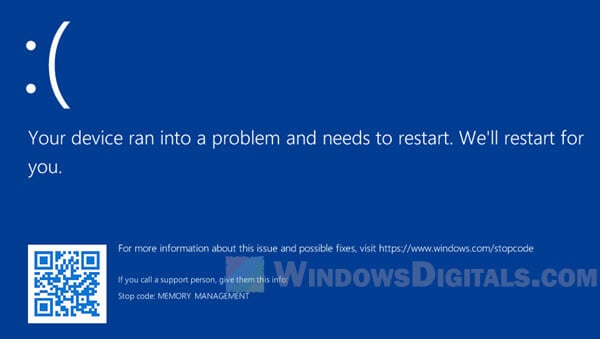
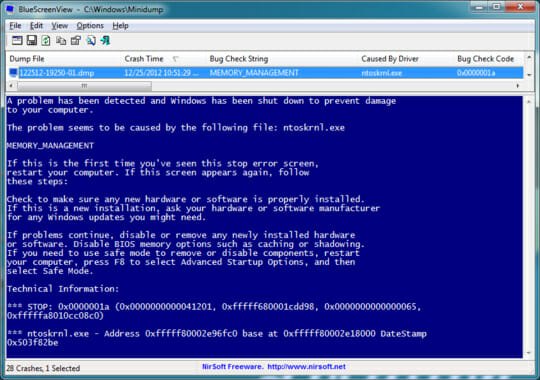

Related Post
NTOSKRNL.Exe Failed: When Windows Core Crumbles
Ntskrnl.Exe.Bsod: The System Crash That Speaks Volumes About Faulty NTOSKRNL

Is Dokumen Pub Safe? Decoding the Secure Digital Document Solution

Dodgers Spring Training Standings Reveal a Competitive Edge — Here’s What’s Next for the Attitude Squad

